Microsoft Defender For Endpoint Linux – This article provides advanced deployment guidance for Microsoft Defender for endpoints on Linux. You will be given a short summary of the implementation steps and the system requirements, and then you will be guided through the actual implementation steps. You will also learn how to verify that the device is installed correctly.
Regarding general guidance for a specific Microsoft Defender for Endpoint on Linux deployment. The applicability of some steps is determined by the requirements of your Linux environment.
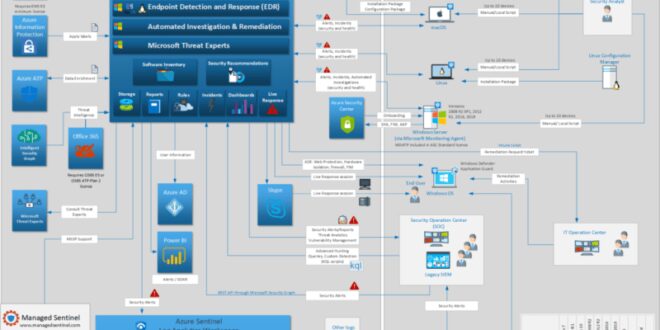
Microsoft Defender For Endpoint Linux

Consider performing the following optional items. While they are not specific to Microsoft Defender for endpoints, they do improve performance on Linux systems.
The Bridge From Intune To Defender For Endpoint
Work with your firewall, proxy, and network administrator to add Microsoft Defender to the allow list for the endpoint URL and prevent SSL inspection from happening.
To prevent man-in-the-middle attacks, all traffic hosted by Microsoft Azure uses certificate pinning. As a result, SSL inspection is not allowed by major firewall systems. You must bypass SSL inspection for Microsoft Defender for the endpoint URL.
Capture performance data from endpoints with Defender for Endpoints installed. This includes disk space availability on all mounted partitions, memory usage, process list, and CPU usage (total for all cores).
Any file system can eventually become corrupted, so before installing any new software, it’s a good idea to install it on a healthy file system.
Microsoft Defender For Endpoint On Aws Ec2
This step of the installation process adds Defender for Endpoints to the exclusion list for your existing Endpoint Protection solution and any other security products your organization uses. You can choose from several methods to add your exclusions to Microsoft Defender Antivirus.
Review the “Common Mistakes to Avoid When Defining Exclusions” sections, folder location, and process for Linux and macOS platforms.
Set up your device groups, device collections, and organizational units Device groups, device collections, and organizational units help your security team manage and assign security policies efficiently and effectively. The following table describes each of these groups and how to configure them. Your organization might not use all three store types.

Device groups are also useful for granting access to these devices so that your security team can take corrective action if necessary.
Use Microsoft Defender For Cloud Apps To Protect Your M365 Tenant
Device groups are created when an attack is detected and prevented. Alerts, such as early access alerts, are triggered and appear in the Microsoft 365 Defender portal.
5. Select an option from the Automation Level list. (We highly recommend automatically remediating threats.) For more information on the different levels of automation, see How Threats Are Remediated.
6. Specify the conditions for a matching rule to determine which devices belong to the device group. For example, you can choose a domain, OS version, or even use a device tag.
7. On the User Access tab, specify the roles that should have access to the devices included in the device group.
Protecting Windows 10 And Other Devices With Microsoft Def…
Device collections allow your security team to manage applications, deploy compliance settings, or install software updates to devices across your organization.
You can then assign administrators to specific organizational units and apply group policies to enforce targeted configuration settings.
Prevents local admins from adding false positives or true positives compatible with threat types (via bash (command prompt)).

High I/O workloads such as Postgres, OracleDB, Jira, and Jenkins may require additional exclusions depending on the amount of activity being processed (which Defender then monitors for the endpoint). If you experience performance degradation after installing Defender for Endpoints, it is recommended that you follow the termination guidelines of third-party application providers. Also note common exclusion errors for Microsoft Defender Antivirus.
Microsoft Defender For Endpoint For Linux Is Coming Soon To Microsoft Defender For Cloud
This download registers Microsoft Defender for Endpoint on Linux to send data to your Microsoft Defender for Endpoint instance.
After downloading this package, you can follow the manual installation instructions or use the Linux management platform to deploy and manage Defender for Endpoints on Linux.
Defender for Endpoints on Linux is designed so that virtually any management solution can easily deploy and manage Defender for Endpoints settings on Linux. Some common Linux management platforms include Ansible, Puppet, and Chef. The following documents provide examples of how to configure these management platforms to deploy and configure Defender for Endpoints on Linux.
A reboot is not required after installing or updating Microsoft Defender for Endpoints on Linux, except when you run AuditD in immutable mode.
Microsoft Defender For Endpoint
Schedule an antivirus scan with Anacron in Microsoft Defender for Endpoints on Linux. For more information, see Schedule an antivirus scan with Anacron in Microsoft Defender for Endpoints on Linux.
Schedule an update of Microsoft Defender for endpoints on Linux. For more information, see Schedule updates for Microsoft Defender for endpoints on Linux.
How do I troubleshoot installation issues with Microsoft Defender for endpoints on Linux?

To verify Microsoft Defender for Endpoint on Linux communication with the cloud using existing network settings, run the following connectivity test from the command line:
Microsoft Defender For Endpoint On Mac Now Offers Better Security Controls For Usb Devices
Microsoft regularly releases software updates to improve performance and security and provide new features. To update Microsoft Defender for endpoints on Linux. For more information, see Deploy updates for Microsoft Defender for endpoints on Linux.
If you have a satellite of Redhat (similar to WSUS in Windows), you can get updated packages from it.
Automate agent updates on a monthly (recommended) schedule using a cron job. For more information, see Schedule updates for Microsoft Defender for endpoints on Linux.
Ideally, you should include one of each type of Linux system you’re running on the preview channel so you can spot compatibility, performance, and reliability issues before pushing the builds to the current channel.
Microsoft Defender For Endpoint Now Secures Unmanaged Devices And Linux Gets Edr
Channel selection determines the type and frequency of updates offered on your device. Devices in beta receive updates and new features first, followed by previews, and finally the current one.
To preview new features and provide feedback more quickly, it is recommended that you configure some devices in your enterprise to use beta or preview.
If you want to switch channels after the initial installation, you must reinstall the product. To switch product channels: Remove the existing package, reconfigure your device to use the new channel, and follow the steps in this document to install the package from the new location.
Run the following identity test to ensure that the device installs correctly and is reported to service:
Microsoft Defender For Endpoint Demonstration Scenarios
If you notice that third-party ISVs, internally developed Linux apps, or scripts are using high CPU usage, take the following steps to investigate the cause.
Now that you’ve identified the process causing the high CPU usage, use the related diagnostic guidance in the next section.
Was identified as the process causing the high CPU usage. Based on the result, you can apply directives to check the wdavdaemon non-privileged process.
Download and run Microsoft Defender for Endpoint Client Analyzer. For more information, see Run Client Analyzer on macOS or Linux.
Install Microsoft Defender For Endpoint: Windows
If you have internal apps/scripts or legitimate third-party apps/scripts that are flagged, Microsoft security researchers analyze suspicious files to determine whether they are threats, unwanted applications, or normal files. Submit files that you believe to be malware or files that you incorrectly classify as malware using the Unified Submission Experience (for more information, see Unified Submission Experience) or Submit Files.
Then your next step is to remove your non-Microsoft anti-virus, anti-malware, and endpoint protection solutions. When uninstalling your non-Microsoft solution, make sure that if you set Defender to passive mode for the endpoint during installation or configuration, you update your configuration to switch from passive mode to active .
Do you want more? Connect with the Microsoft security community in our tech community: Microsoft Defender for Endpoint Tech Community. Turn on suggestions Automatic suggestions help you quickly refine your search results by suggesting possible matches as you type.
When it comes to protecting servers in hybrid and multi-cloud environments, Microsoft Defender for Servers as part of Microsoft Defender for the Cloud is the solution you may be looking for. However, with all the features, dependencies, and complexities, it can be challenging to always make the right decisions when planning, integrating, and deploying Defender to servers in your environment. With this blog, we focus on deploying and integrating Microsoft Defender for Endpoints with Microsoft Defender for Servers on Linux machines.
What Is Windows Defender Atp & Is It Any Good?
Microsoft Defender for Servers is available in two different plans, including integration and automated deployment of Microsoft Defender for Endpoints for both Windows and Linux machines.
For more information, see this table on supported features for VMs and servers in Defender for Cloud. For more information about the features of the Defender for Server subscription, please refer to this document.
The Microsoft Defender for Endpoints for Linux integration is expected to launch in Defender for Servers in Summer 2021. At this point, Defender for Endpoint Integration for Windows Server has been part of the product for quite some time, and with the introduction of Linux support, we added an opt-in way for existing customers to decide when they want to be protected on their Linux machines .wants to enable integration and deployment for . From that point forward, Defender will be endpoint integration ready for Windows and Linux.
Microsoft defender for endpoint for linux, microsoft defender for endpoint, microsoft defender endpoint security, microsoft defender endpoint, microsoft defender for endpoint pricing, microsoft defender for endpoint edr, microsoft defender for endpoint onboarding blob, microsoft defender for endpoint on linux, microsoft defender for endpoint cost, microsoft defender for endpoint api, microsoft defender for endpoint portal, microsoft defender for endpoint business premium